Thales Luna Network HSM
Luna Network Hardware Security Modules (HSMs)
Secure your sensitive data and critical applications by storing, protecting and managing your cryptographic keys in Thales Luna Network Hardware Security Modules (HSMs) – high-assurance, tamper-resistant, network-attached appliances offering market-leading performance.
Contact us to learn how you can integrate Luna Network HSMs into a wide range of applications to accelerate cryptographic operations, secure the crypto key lifecycle, and provide a root of trust for your entire encryption infrastructure.
Approach to Key Security: Keys in Hardware
Protect the entire lifecycle of your keys within the FIPS 140-2 validated confines of the SafeNet Luna Network HSM. Our unique approach to protecting cryptographic keys in hardware positions our appliances as the most trusted general purpose HSMs on the market. Unlike other methods of key storage which move keys outside of the HSM into a “trusted layer,” the keys-in-hardware approach ensures that your keys always benefit from both physical and logical protections of the SafeNet Luna Network HSM.
Market-Leading Performance – Built for Speed
Faster than other HSMs on the market, SafeNet Luna Network HSM 7 is ideally suited for use cases that require high performance such as the protection of SSL/TLS keys and high volume code signing.
Scalable Security for Virtual and Cloud Environments
Separate SafeNet Luna Network HSMs into up to 100 cryptographically isolated partitions, with each partition acting as if it was an independent HSM. A single HSM can act as the root of trust that protects the cryptographic key lifecycle of hundreds of independent applications, providing you with a tremendous amount of scalability and flexibility.
Keys and partitions are cryptographically separated from each other, enabling Enterprises and Service Providers to leverage the same hardware for multiple tenants and appliances.
Ease of Use – Centralized Crypto Resources
Simplify the administration of multiple HSMs using SafeNet Crypto Command Center to provide on-demand provisioning and monitoring of crypto resources.
The De Facto Standard for the Cloud
As the de facto standard in the cloud, SafeNet Luna Network HSMs are deployed in more public cloud environments than any other HSM. Scale to meet your cryptographic performance requirements regardless of the environment be it on-premises, private, public, or hybrid and multi-cloud environments.
Largest Ecosystem of Partners Available
Quickly secure a large number of standard applications with our broad partner ecosystem – documented, out-of-the-box integrations with SafeNet Luna Network HSMs.
Internet of Things
Guard against evolving threats and capitalize on emerging technologies including the Internet of Things (IoT), Blockchain , and more, with Gemalto’s unparalleled combination of products and features.
Compliance
Meet compliance and audit needs for GDPR, eIDAS, FIPS 140, Common Criteria, HIPAA, PCI-DSS, and others, in highly-regulated industries including Financial, Healthcare and Government.
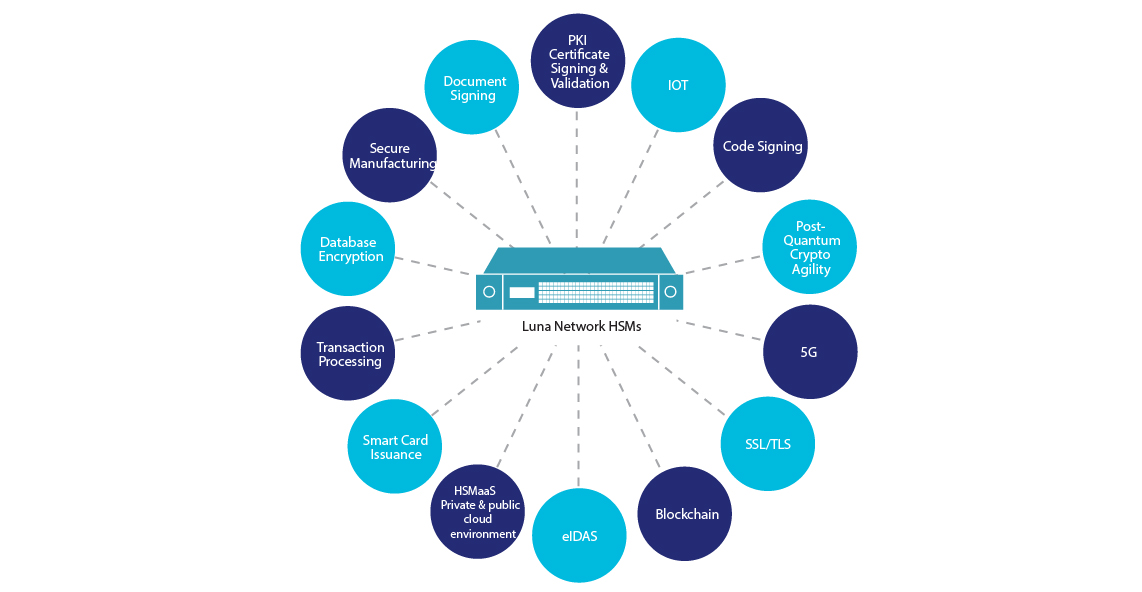
Sample Applications
- PKI key generation & storage (online and offline CA keys)
- SSL/TLS
- Code Signing
- Certificate Signing & Validation
- Document signing
- HSMaaS – Private & Public Cloud Environment
- Transaction processing
- Database encryption
- Smart card issuance
- Hardware root of trust for the Internet of Things (IoT)
- Blockchain
- Compliance including GDPR, PCI-DSS, HIPAA, eIDAS, and more
Security at a Glance
- Keys always remain in FIPS 140-2 Level 3-validated, tamper-evident hardware
- High-assurance delivery with secure transport mode
- De facto standard for the cloud
- Multiple roles for strong separation of duties
- Multi person MofN with multi-factor authentication for increased security
- Meet compliance needs for GDPR, HIPAA, PCI-DSS, eIDAS, and more
- Secure audit logging
- Remote management
- Multi-part splits for all access control keys
- Strongest cryptographic algorithms including Suite B algorithm support
- Secure decommission
Features
- Dual Hot Swap Power Supplies
- Field Serviceable Components
- Software upgradable
- Multiple Roles for Administration
- Strong Separation of Duties
- Partitioning and strong cryptographic separation
- Load Balancing and Scalability



 ไทย
ไทย